How do I Secure External Elasticsearch Communication using HTTPS with X-Pack?
You can use X-Pack to secure external Elasticsearch to communicate securely over HTTPS. This section explains the steps required to configure X-Pack for API Gateway.
Before you begin
Ensure that you have installed an updated version of Java in your system and configure the path of the environment variable.
To secure External Elasticsearch communication using X-Pack
1. Shut down API Gateway.
2. Open the elasticsearch.yml file from the SAG_Install_Dir\profiles\IS_instance_name\apigateway\config folder.
3. Set the property xpack.security.enabled to true.
4. Save the changes.
a. Enable external Elasticsearch security features.
b. Generate the certificate authority.
c. Encrypt internode communication with TLS.
d. Set passwords for built-in users.
e. Configure external Kibana to connect to external Elasticsearch with a password.
f. Set up basic security for the Elastic stack plus secured HTTPS traffic.
g. Encrypt HTTP client communication for external Elasticsearch.
h. Encrypt HTTP client communication for external Kibana.
External Elasticsearch now runs on a HTTPS port and requires basic authentication to access.
Configure External Kibana to connect to External Elasticsearch
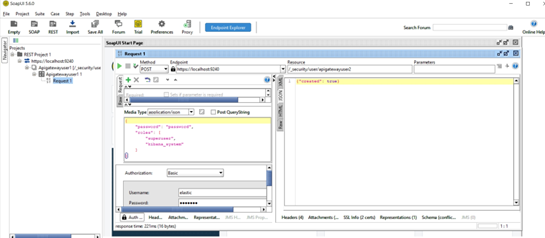
1. Create a new user to access external Kibana.
3. Open the uiconfiguration.properties file from the SAG_Install_Dir\profiles\IS_instance_name\apigateway\config folder. Set the property apigw.kibana.autostart to false and save the changes.
4. Open the kibana.yml file from the SAG_Install_Dir\profiles\IS_instance_name\apigateway\dashboard\config folder and set the following.

elasticsearch.username :
Elasticsearch username
elasticsearch.password :
Elasticesearch PasswordExample:

elasticsearch.username : "apigatewayuser2"

elasticsearch.password : “Password"
Update Keystore and Trustore
1. Export the external Elasticsearch certificate from the keystore
a. Open the command prompt from the location SAG_Install_Dir\elasticsearch-ssl-http\elasticsearch folder.
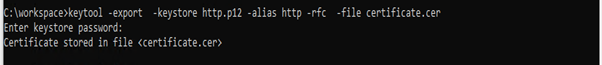
b. Run the following command to export the certificate from the keystore and place it in the required location. :
keytool -export -keystore http.p12 -alias http -rfc -file certificate.cer
d. Enter the password for the keystore
The certificate is exported and saved with the name you provide.
2. Import the certificate into the truststore
a. Open the command prompt from the location SAG_Install_Dir\elasticsearch-ssl-http\elasticsearch folder.
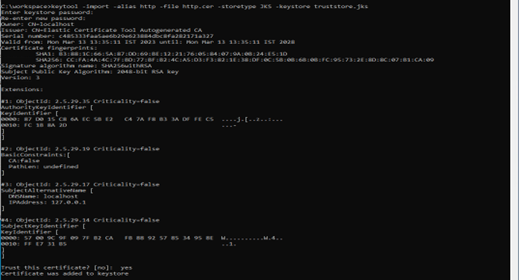
b. Run the following command to import the generated certificate into the truststore :
keytool -import -alias http -file certificate.cer -storetype JKS -keystore truststore.jks
c. Enter the password for the Keystore setup in step
The exported certificate is saved in the specified location.
Update API Gateway configurations to connect to external Elasticsearch
1. Open the config.properties file from the SAG_Install_Dir\IntegrationServer\instances\instance_name\packages\WmAPIGateway\config\resources\elasticsearch folder.
2. Remove the # symbol from the following properties and provide the corresponding values for the properties and save the file.
Property | Value to be set |
pg.gateway.elasticsearch.http.username | External Elasticsearch username |
pg.gateway.elasticsearch.http.password | External Elasticsearch password |
pg.gateway.elasticsearch.https.truststore.filepath | <Elastic_Dir>/sagconfig/truststore.jks |
pg.gateway.elasticsearch.https.truststore.password | password of trust store |
pg.gateway.elasticsearch.https.enabled | true |
3. Start external Elasticsearch.
4. Veify if external Elasticsearch is up and running, start the external Kibana server by running the kibana.bat file located at SAG_Install_Dir\profiles\IS_default\apigateway\dashboard\bin.
5. Start API Gateway.
You can now log on to API Gateway and access the Analytics page without any challenge.